Secure and Reliable Information Administration With Cloud Provider
In the ever-evolving landscape of information administration, the use of cloud solutions has become a crucial service for companies looking for to strengthen their information security actions while improving operational effectiveness. universal cloud Service. The complex interplay between securing delicate details and making certain seamless access positions a complicated obstacle that companies should navigate with diligence. By checking out the nuances of safe and secure information administration via cloud solutions, a much deeper understanding of the innovations and approaches underpinning this paradigm shift can be revealed, shedding light on the complex advantages and factors to consider that form the modern data administration environment
Relevance of Cloud Providers for Information Administration
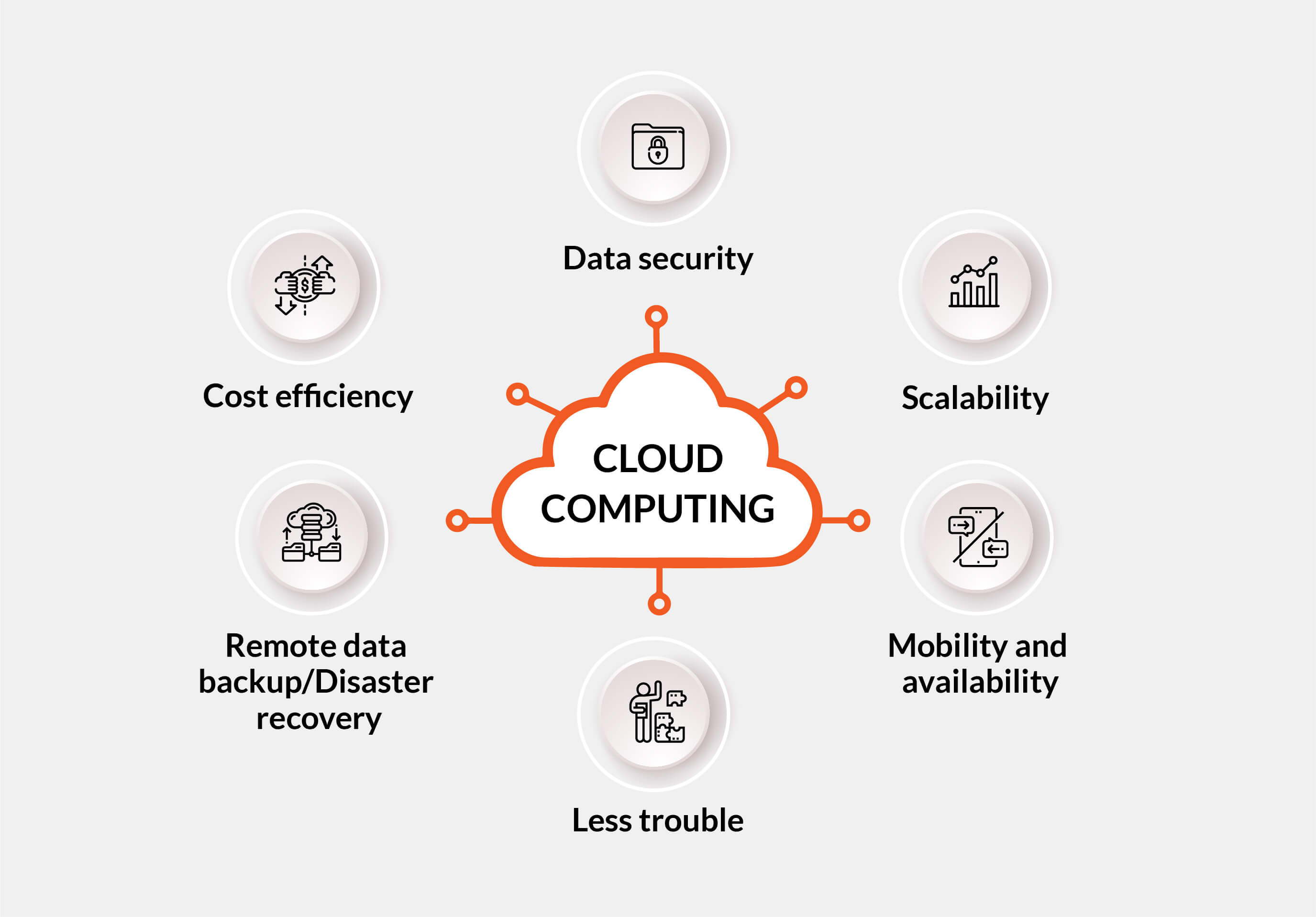
Cloud services play an essential role in modern data monitoring practices due to their scalability, cost-effectiveness, and availability. Additionally, cloud solutions give high ease of access, allowing individuals to accessibility data from anywhere with a net connection.
In addition, cloud solutions use cost-effectiveness by eliminating the requirement for buying costly equipment and maintenance. Organizations can go with subscription-based models that line up with their spending plan and pay only for the sources they utilize. This assists in lowering ahead of time expenses and total functional expenses, making cloud solutions a practical choice for organizations of all sizes. In significance, the significance of cloud solutions in information monitoring can not be overemphasized, as they provide the needed devices to simplify operations, enhance partnership, and drive organization development.
Trick Safety And Security Challenges in Cloud Information Storage Space
To resolve these protection difficulties, companies require durable safety and security measures, including encryption, access controls, regular safety and security audits, and personnel training. Partnering with trusted cloud company that provide sophisticated safety and security features and conformity certifications can additionally aid reduce threats connected with cloud data storage. Eventually, a aggressive and extensive strategy to protection is vital in protecting information stored in the cloud.
Implementing Data Security in Cloud Solutions

Implementing data file encryption in cloud services includes utilizing robust security algorithms and safe key administration techniques. Encryption tricks need to be saved separately from the encrypted data to add an extra layer of defense. Furthermore, organizations must on a regular basis update security secrets and utilize solid accessibility controls his explanation to limit who can decrypt the data.
Additionally, data file encryption need to be used not just during storage however also during data transmission to and from the cloud. Safe and secure communication procedures like SSL/TLS can assist safeguard information in transit, guaranteeing end-to-end file encryption. By prioritizing information security in cloud remedies, companies can bolster their data safety and security posture and keep the confidentiality and stability of their sensitive information.
Best Practices for Data Backup and Recovery
Furthermore, conducting normal healing drills is crucial to check the efficiency of back-up treatments and the organization's capacity to restore information promptly. Automation of backup procedures can enhance operations and lower the capacity for human mistake. Encryption of backed-up information adds an extra layer of protection, safeguarding delicate information from unapproved gain access to throughout storage and transmission. By following these finest methods, companies can boost their data strength and make sure smooth operations despite unpredicted events.
Tracking and Bookkeeping Information Access in Cloud
To keep data integrity and protection within cloud atmospheres, it his response is crucial for organizations to develop robust measures for surveillance and auditing data access. Bookkeeping data accessibility goes a step better by supplying a detailed document of all data accessibility activities. Cloud solution suppliers commonly supply devices and services that assist in monitoring and auditing of information gain access to, permitting companies to gain understandings right into exactly how their information is being utilized and making sure responsibility.
Verdict
Finally, cloud solutions play a vital role in making sure secure and effective information management for services. By addressing essential protection challenges with information encryption, backup, recuperation, and keeping track of techniques, organizations can shield sensitive info from unapproved access and information violations. Implementing these best methods in cloud services advertises information integrity, confidentiality, and availability, inevitably boosting partnership and performance within the company.
The vital security challenges in cloud data storage revolve around data breaches, data loss, conformity regulations, and data residency problems. By securing information prior to it is posted to the cloud, companies can minimize the threat of unauthorized gain access to and data breaches. By prioritizing data encryption in cloud solutions, organizations can strengthen their data security posture and maintain the discretion see this and honesty of their delicate information.
To maintain information honesty and safety within cloud atmospheres, it is crucial for companies to develop durable steps for monitoring and bookkeeping information gain access to. Cloud service suppliers usually use devices and services that facilitate surveillance and bookkeeping of information access, permitting organizations to gain understandings into how their data is being utilized and making certain responsibility.